Overview
The Microsoft 365 Discovery Report is a collection of outputs from the various workloads inside a Microsoft 365 tenant, all consolidated into a single Excel based report. It details the following workloads.
- Exchange Online Mailboxes (Users/Shared/Resources) – All Info
- OneDrive Usage
- SharePoint Sites
- SharePoint Libraries
- Teams – including Channels/Memberships/Data Usage
- MFA details
- Distribution Lists and Members
- Contacts
- Guest Accounts
- Unified Groups and Members
- Security Groups and Members
- Azure AD Devices
- Password Expiration Details
- License Information and Consumption
- Public Folders
- MX Records
- Transport Rules
- Send/Receive Connectors
- Planner(s)
It is all performed by using a locally based PowerShell 7 script that runs on your own infrastructure, connecting to the various workloads directly from there.
The report gives a solid tenant landscape and is intended to be used in preparation for a migration effort. By using the outputs, various batching and grouping techniques can be used, making the planning easier than using the normal Microsoft 365 Admin Center and the reports contained there.
The latest version is V7.14, released on 21 May 2025
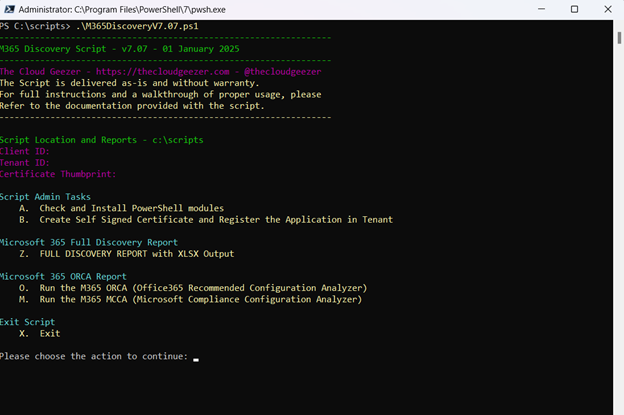
Getting all that information can normally involve a load of different scripts and console items to view which is why I have put it all together into a single script. The script runs across the tenant and creates multiple CSV files with all the data, then it compiles everything into a single Excel sheet with multiple tabs, all formatted and looking nice.
It even installs automatically all the PowerShell modules for Microsoft 365 that are required to connect and run everything. The modules required are
- Microsoft Graph
- Exchange Online
- Import-Excel (Used for the Excel Output at the end)
Important Note: Everything is read from the tenant only, absolutely nothing is written there.
Administrative rights required
On the source tenant where the report is being run the account connecting to the M365 Modules will need to have the following administrative rights assigned to it. This is for the Exchange Online module only, as the rights in Graph are given to the Application Registration specifically and are not based on an account login.
- Global Reader
If the admin user that is running the report has Global Admin rights on the tenant, then no other rights need to be added.
To perform the Application Registration at the start, to setup the connection to the tenant, you will need to connect with the appropriate Azure AD / Entra ID rights in order to create the application.
As the script runs it will connect to Microsoft Graph and perform all the work. It does need a small amount of data from the Exchange Online PowerShell Module and will connect to that right at the start.
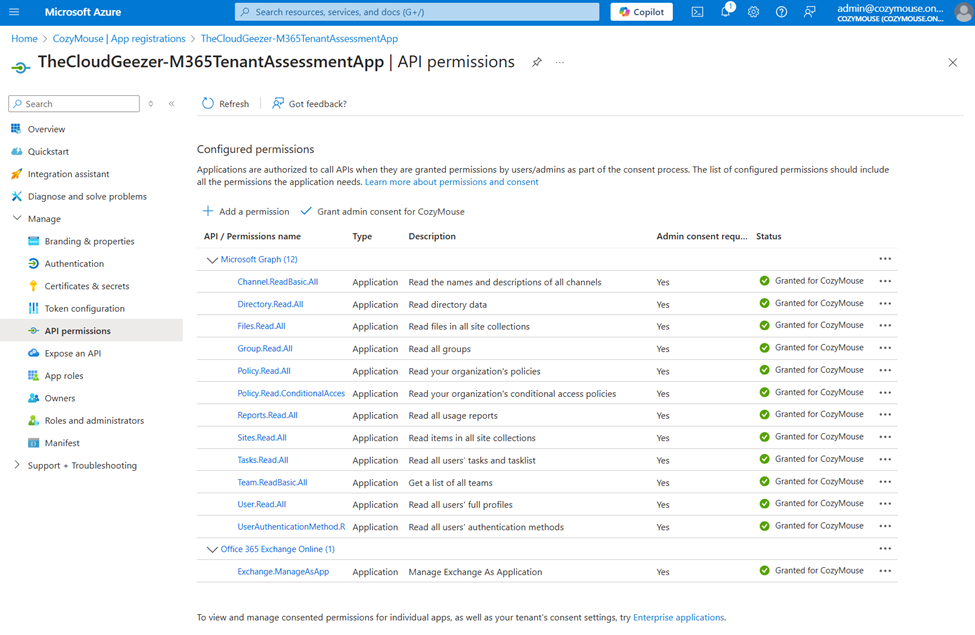
Application Registration
To use the MS Graph connections, the script works with an Application Registration so that you can define the rights that the script has access to inside the tenant. The script has the option to perform the Application Registration itself and will update the config files accordingly. As a summary, the access requirements look like this.
ORCA / MCCA Report
In the update in December 2023, the tool includes the ability to run the Microsoft ORCA report from inside the script. The ORCA Report is the Office 365 Recommended Configuration Analyzer and gives solid information and recommendations for the tenant with regard to mail/inbound/outbound security. An example is here.
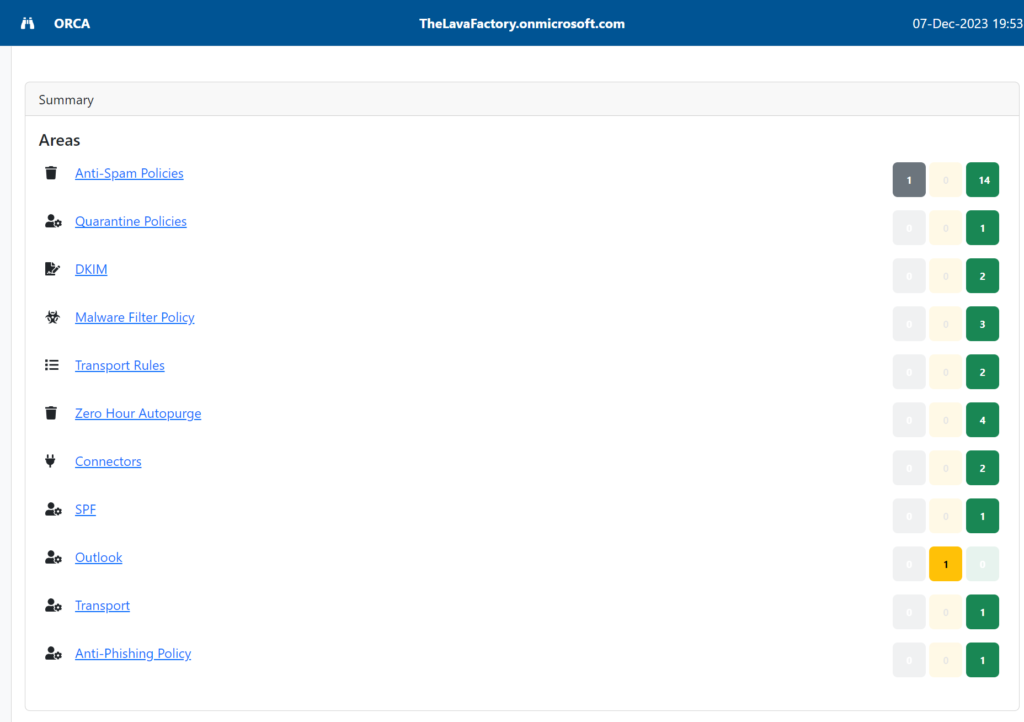
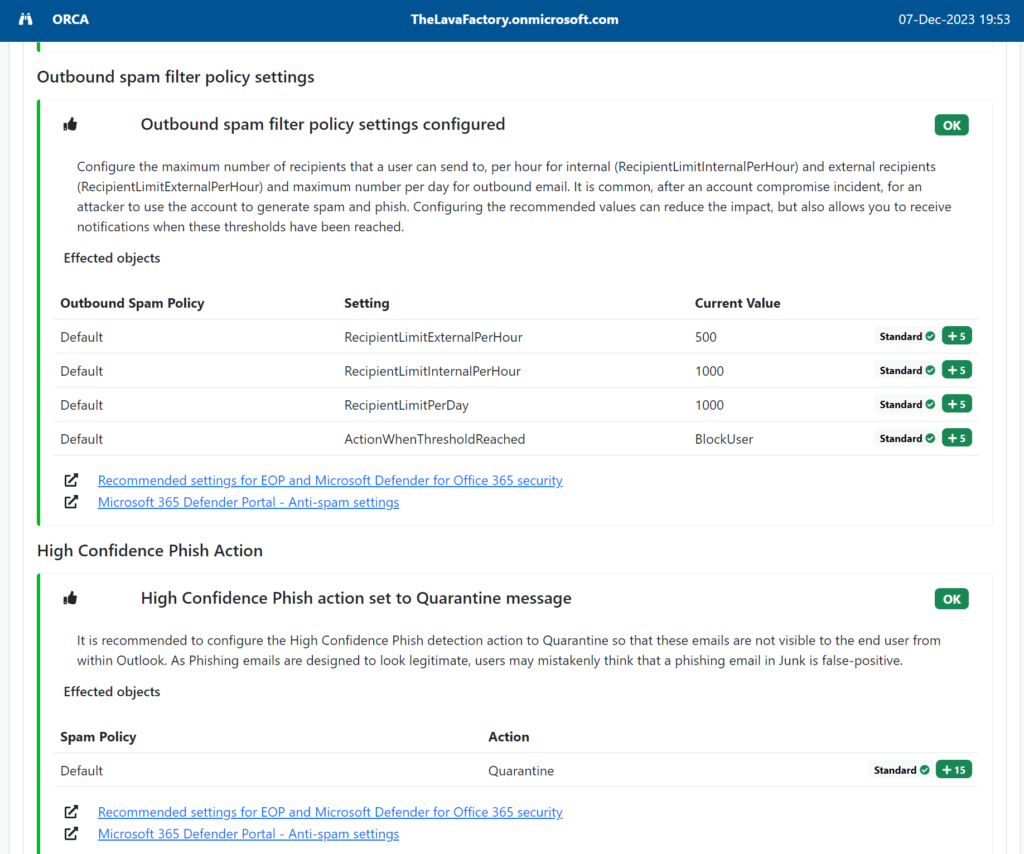
An extremely useful report when looking at your own, or a clients, tenant. Likewise, the MCCA report was also added and can be triggered from the main menu. This gives a great couple of additional reports that are always interesting and well received by the client that you are running this for on their tenant.
https://store.thecloudgeezer.com/products/microsoft-365-discovery-script
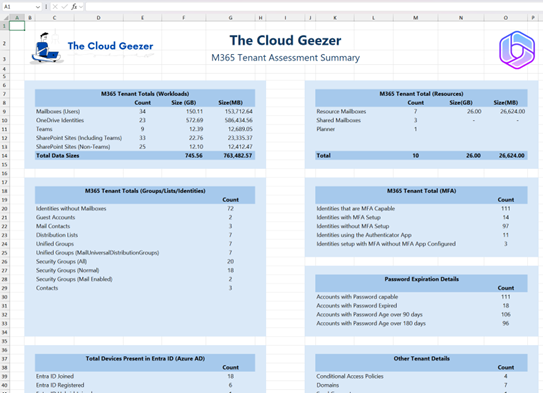
The Output & Tool
Here is an example of the output you can expect. Many columns are included, not just what is shown on the limited space below.
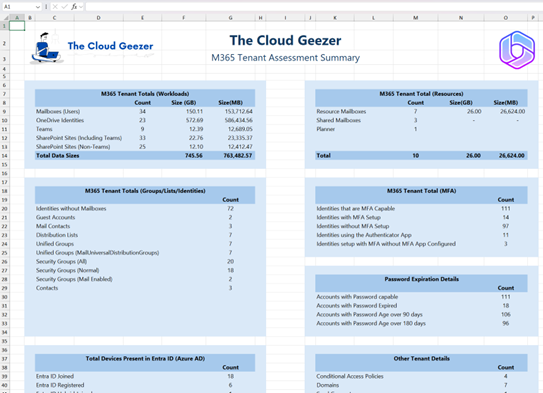
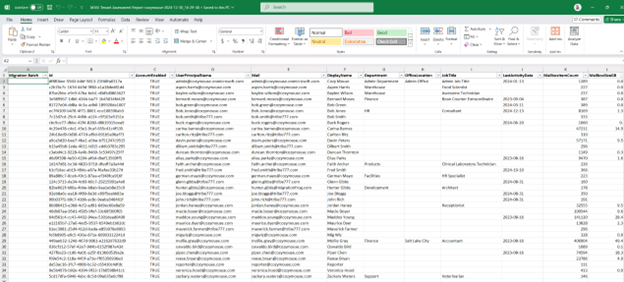
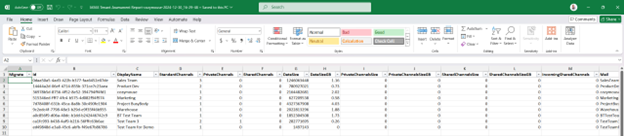
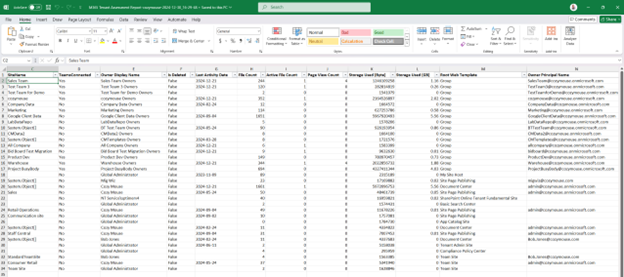
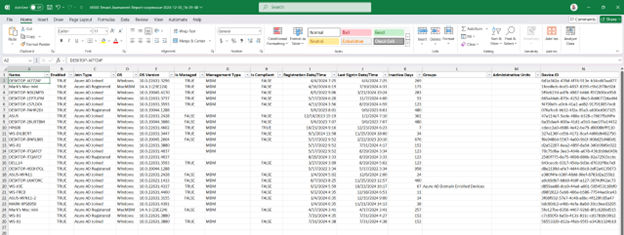
Everything is run from a simple menu to make it easy to get the output you need.
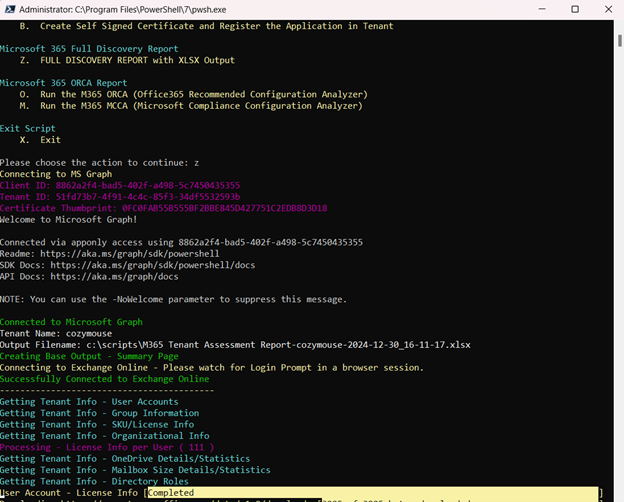
Downloading and Running
The script comes in the form of a ZIP file which allows you to extract the .PS1 file on to your machine. It is recommended that it be run from the c:\scripts directory on your local machine. If you want to change the output then the first few lines of the script have the location where you can change this.
When you run the PowerShell session to run the script it is important that you “Run As Administrator” when you start it. This is a requirement of the PowerShell modules that Microsoft 365 uses to connect to the cloud and you will find that they will fail without the local administrator privileges.
Discount
To get a 50% discount code for this script, subscribe to my YouTube channel and then drop me an email to mark@thecloudgeezer.com and I will send you a coupon code.
https://youtube.com/thecloudgeezer
All the scripting products, and the CloudOCM system, are available in the store.
https://store.thecloudgeezer.com
Hope you find this useful, please reach out in the comments with any thoughts, comments or improvements you would like to see.
Mark – The Cloud Geezer – mark@thecloudgeezer.com

